Cybersecurity projects.
FTP Attack
ARP poisoning
Spear Phishing (Social engineering)
SMB attack with remote code xexcution via social engineering and DoS attack
HackerOne Bug Bounty program.
During my free time, I like to participate in bug bounty program. Recently, I found a vulnerability at a KPOP audition website that have CVE-2007-6750 and reported it via the HackerOne platform.
F Society.
Inspired by the movie MR ROBOT, Fsociety was a tool I contributed during DEFCON 28. As part of røøtz Asylum(A place where kids learn white-hat hacking to better the world) we created this simplified penetration's testing tool for kids to understand easier.
Brute-force Dictionary attack.
I learnt to execute brute-force attacks during my free time. Using Burpsuite, I used Kali Linux (attacking machine) & metasploitable (Target Machine) and Hashcat. I was able to hack into “John’s account”.
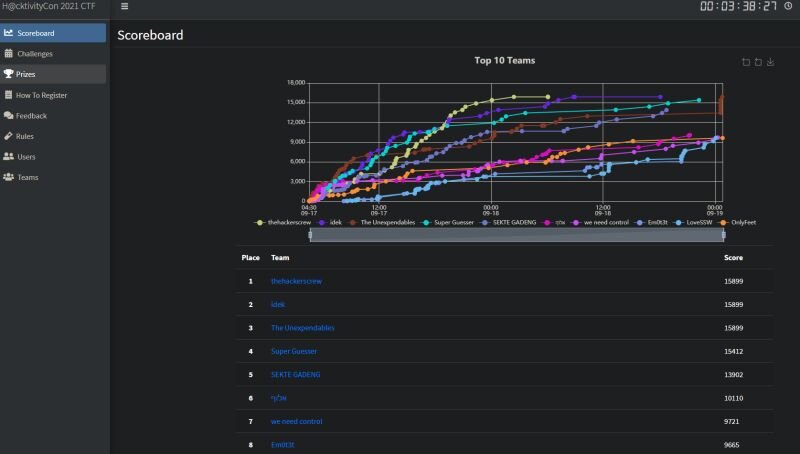
HACKTHEBOX
HACKTHEBOX is an online cybersecurity training platform that allows me to network with other ethical hackers as well as joining and practicing for CTF competitions and penetration testing.
AlienVault SIEM
I have been keeping up to date with latest Cybersecurity news and evolving threats not only by watching the news but subscribing to various SIEM Open source threat exchange platforms such as AlienVault.
SYNFlooding dos attack
Using metasploit framework, I used auxiliary/dos/tcp/synflood module to execute the synflooding attack.
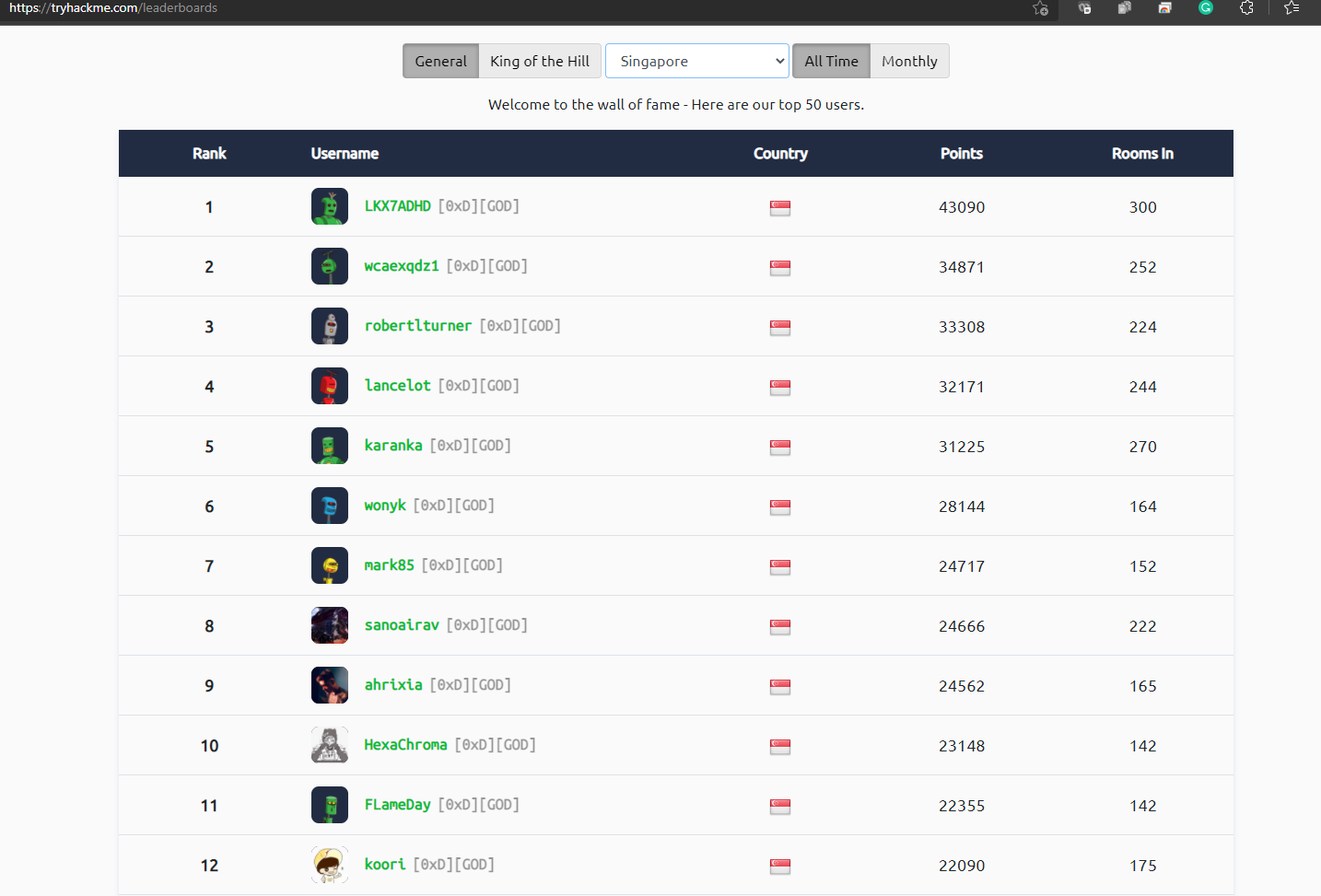
Try Hack Me
Top hacker in Singapore
FTP Attack mitigation
ARP poisoning mitigation
Spear phishing mitigation ( Social engineering)
Mitigating malicious Sources
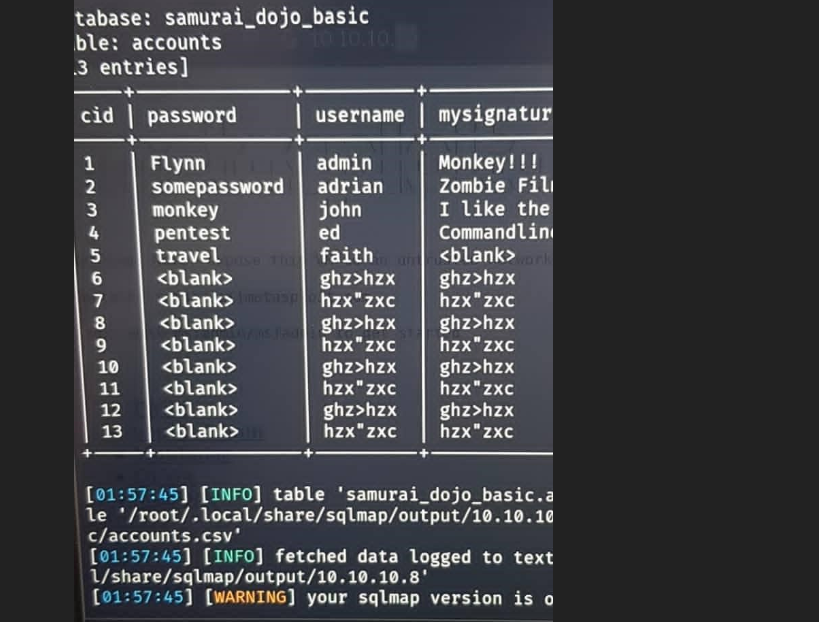
SQL enumeration.
I learn SQLMap during my free time. Using Kali Linux (attacking machine) & metasploitable (Target Machine, Web server) I was able to identify and exploit the SQL injection flaws.
Android Hacking.
I learnt Multi/handler tool during my free time and demonstrated the dangers of downloading malicious applications on android phones. Using this tool, I was able to carry out Man-In-The-Middle attacks, Reverse TCP, perform an involuntary backup, take full control of the android phone using Metasploit shellcode.
ARP Poisoning Attack.
I learnt how to execute ARP poisoning attack during my free time from youtube. Using Ettercap in Kali Linux (attacking machine) & metasploitable (Target Machine) I was able to intercept the password by spoofing the MAC address.
Research with Library books.
I have been constantly expanding my knowledge on computer penetration testing, forensics, network security and security operations not only through the internet but also borrowing books from the library.
FTP backdoor command execution
Using metasploit framework, I used exploit/unix/ftp/vsftpd_234_backdoor module and cmd/unix/interact payload to execute the FTP backdoor command execution.
ImmersiveLabs
Top 3 in my cohort in 2020
Other Projects
Startup Weekend Singapore - I was one of the mentor to recommend cybersecurity solutions to 750 participating members from 43 different countries.
Mosque Tech challenge - using micro-bit, my team and I was able to make an app that allow elderly to exercise at home by hitting on the micro-bit sensor.
Universal Drones Singapore (UDS) - Universal Drones Singapore is a non-profit group created by me and my friends to educate drone novice by providing tutoring sessions, a platform for drone enthusiast to meet and level up their skills and to educate safety regulation for aerial activities in collaboration with CAAS ( Civil Aviation Authority of Singapore).
Hackathon@SG - Together with my team of 5, we created sustainable automatic plant watering system using Arduino.
OneMaker Group (OMG) - I was one of the volunteer to teach kids how to use DJI Robomaster.
Life @ ITE
Cybersecurity Student
The modules I learn as part of my Higher National institute technical education on Cyber & Network Security helped me develop a greater understanding in Cyber and Network security systems and exposed me to the necessary skills that a Network Security associate require in today's fast-paced digital era. Such as providing technical support for servers, networks as well as perform vulnerability scanning, and incident monitoring and reporting.
Core Modules.
Computer Management - Install & configure operating System, peripherals & troubleshooting.
Enterprise Networking - Configured Cisco 1941 Router & 2960 switches. OSPF, VLANS, ACL & NTP.
System Administration - Configured Active directory services for Windows 2012.
Virtualization - Configured VMware workstation, ESXi 6.0, vCentre & vMotion.
IT Security - Configured Fortigate firewalls, Intrusion detection system (IDS) & data encryption technologies.
Security Operations - Cybersecurity laws, basic SIEM systems, penertration testing, vulnerability assessment & patching.
Linux - Configured Apache web server NFS, FTP, backup & scripting on Debian 9, Ubuntu & kali linux.
Python Scripting - Basic print, variable, class & file operations using PyCharm.
Some Photos taken during project presentations.
Sys admin presentation
Implementing Active directory.
I.T Security Presentation.
Picture of me (in black jacket) with my groupmate explaining how we simulate a penetration testing, vulnerability report and Security systems implementations.
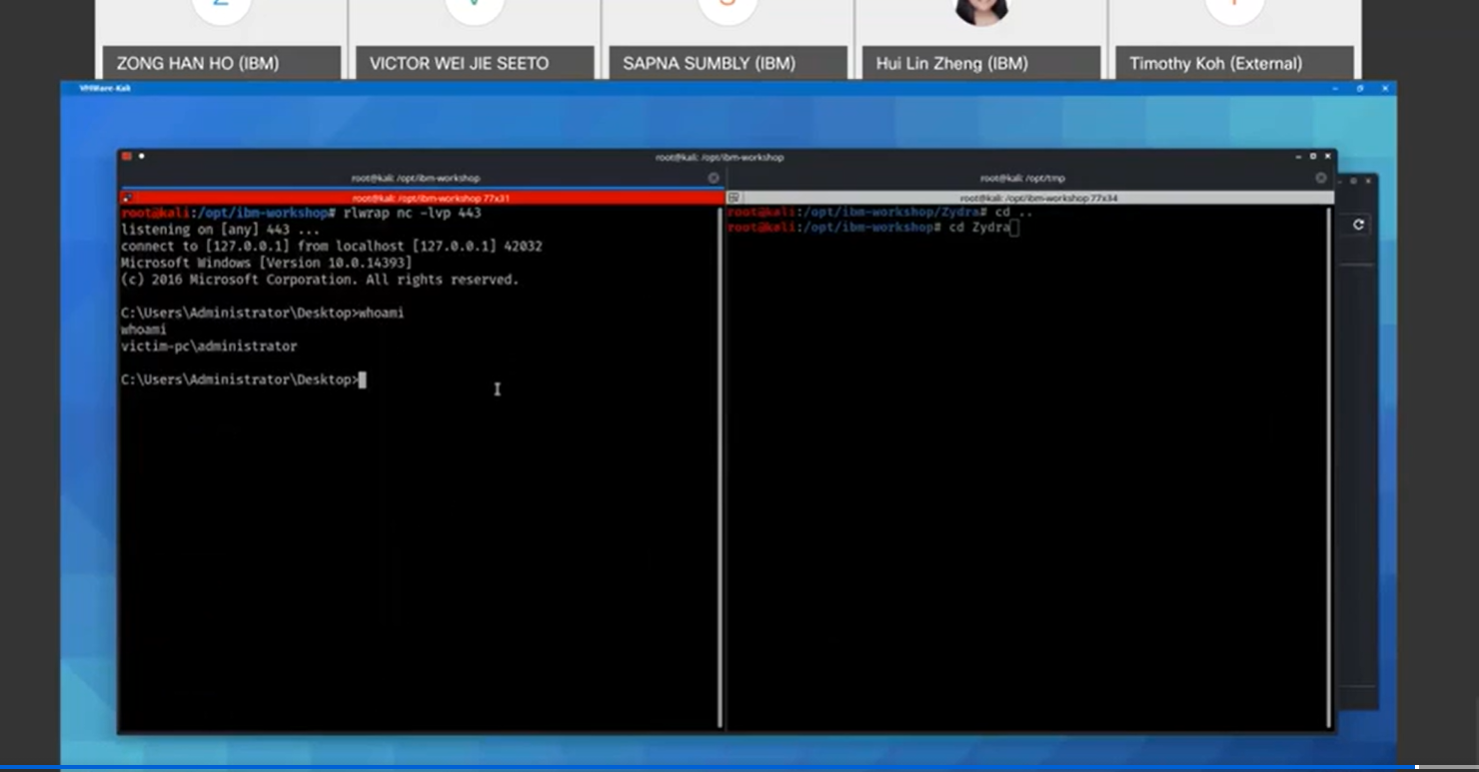
Sec Ops presentation
During my Sec Ops presentation, I also show how a Windows 11 Machine can be hacked using Multi/Handler and MSFVENOM.
Explaining sys admin project
Picture of me explaining the deployment of active directory group policy for a given requirements to my class.
Sec Ops presentation
Picture of me discussing and explaining how ARP poisoning attacks are executed.
Sec Ops presentation
Vulnerability scanning for sec ops project
Cybersecurity Club - CCA & Robotics projects.
Being the president of my school cybersecurity club, I get to work with other like-minded individuals and give lessons on cybersecurity which excites me to learn more!
As the group leader of multiple Hackathons and tech competitions has helped me gain valuable leadership, communication and planning skills.
I led my team to win at the National Robotics competition, Hackaton@SG and GovTech CTF.
I helped my school library program a robot (Temi) which assisted with library operations and enforcing safe distancing measures using AI and machine learning.
Some snapshots and photos of Cybersecurity Club & Robotics projects.
Session on how to execute google dorking and perform OSINT investigation.
Session on how to stay secure and improve privacy online.
Temi robot
A robot I made, assisting with library operations and enforcing safe distancing measures using AI and machine learning.
Face Mask detection using jupyter notebook and help from Github.
Later deployed on a robot (Temi) which assisted with library operations and enforcing safe distancing measures.
National Robotics Competition Team.
Led my team to win Top 10 out of 200 schools.
National Robotics Competition.
Led my team to win Top 10 out of 200 schools.
IBM P-TECH mentorship
About:
IBM P-TECH is a IBM-ITE-Polys partnership and global education program that help population prepare for “new collar” roles such as Cybersecurity Specialist, Application Developer and Cloud Engineer. to strengthen reginal economies.
My experience with P-TECH Mentorship
Being part of the P-TECH program has been an eye-opening experience as I get to attend workshops that are not only related to (STEM) disciples but also cultivating soft skills and self-awareness through the mindfulness and communication workshops.
I get to attend weekly workshops such as Industry visits, in-depth technical skills and workplace competency training. As well as a 1 to 1 mentor to guide me through my Journey for Cybersecurity too.
Being a Cybersecurity student, sometimes there could be concepts and terms I can't understand and P-TECH cybersecurity workshops helped me understand better. Recently, I passed CEH ( Certified Ethical hacker) and SOC ( Security Operations Centre) analyst certification on my own with some guidance from my P-TECH mentor who have experience doing I.T related certifications exams.
Some photos during IBM P-TECH workshops.
data hackathon with Deloitte mentor volunteers.
IBM Cybersecurity workshops on SIEM and Forensics.
CSA (Cybersecurity Agency) site visit.
App dev apprentices workshop.
Motivation and Self-Management workshop.
Demonstration of how man-in-the-middle and rainbow table attacks are done.
GovTech site visit.
Certificate of Attendance.
Testimonials.
ITE Testimonial
Written by class advisor.
IBM P-TECH Testimonial
By Main coordinator, Liaison Manager.
Secondary School testimonial
By Form teachers.